Encryption in Transit
·
TLS /SSL
Encryption at rest
·
Server side encryption
o SSE
S3 : S3 Managed Keys
o SSE
KMS : AWs Managed Service - Key Managed Service
o SSE-C : Customer Provided Keys
·
Client side encryption

Authentication
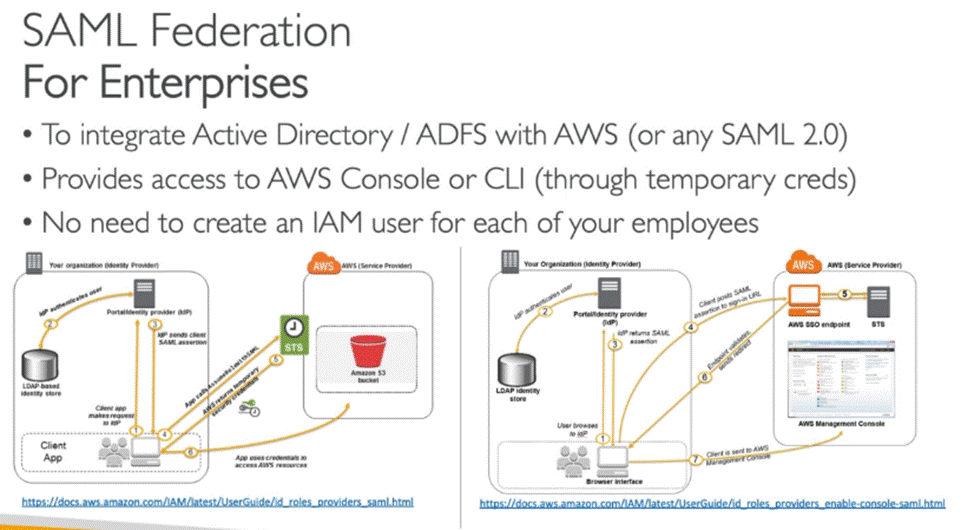
Security Assertion Mark-up Language (SAML, pronounced sam-el) is an open standard for exchanging authentication
and authorization data between parties, in particular, between an identity
provider and a service provide
webidentity
is web based sites, amazon, google,
fb et -any openID connect
OpenID Connect 1.0 is a
simple identity layer on top of the OAuth 2.0
protocol. It allows Clients to verify the identity of the End-User based on the
authentication performed by an Authorization Server, as well as to obtain basic
profile information about the End-User in an interoperable and REST-like
manner.
SSO
(Single Sign On): One login managed by AWS to log in to various business SAML
2.0-compatible applications (office 365 etc)
·
Permission
set: the time the user can log in without the need to
re-login, default is 1 hr, max is 12hr
·
Context
aware: 2 step authentication where verification code is
sent to email as location via browser and
device is examined in the SSO process
·
via
on-premise Active Directory
1.
utilizing Direct Connect> create 2 way trust relationship
STS Security
Token Service > temp access for h1 to aws
resources | cross account access
AWS Directory Service AD Connector
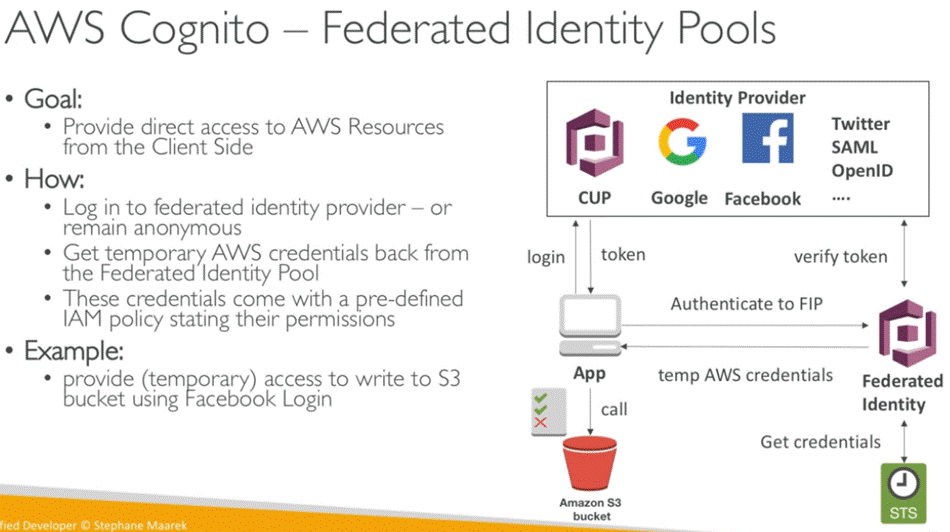
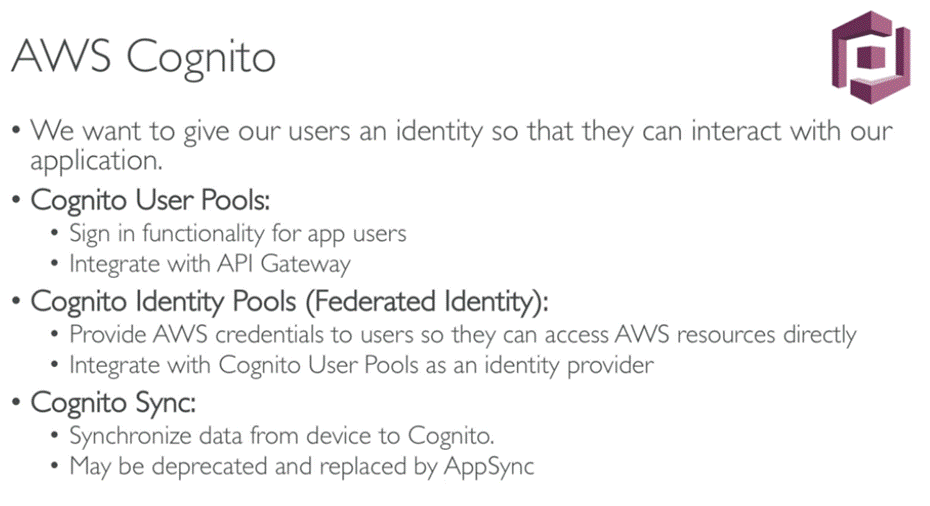
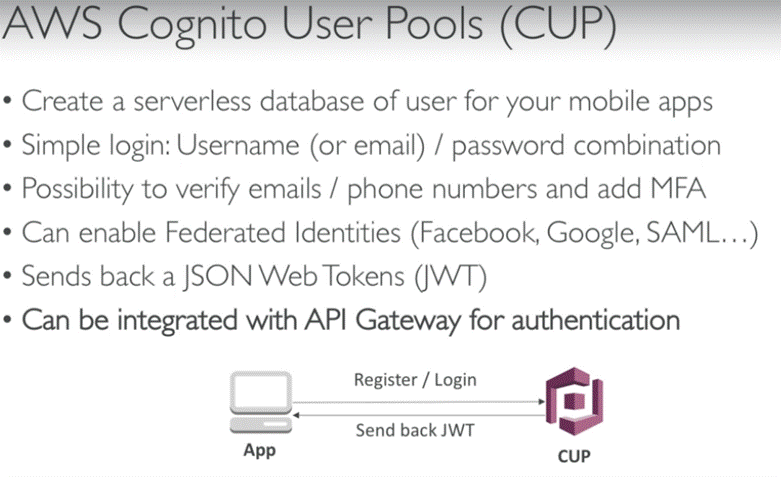
COGNITO
PCI DSS
I.
Install and Configure a firewall to protect card Holder data
II.
Do not use vendor supplied defaults for System passwords and other
security parameters
III.
Protect stored cardholder data (eg encrypt DB at Rest )
IV.
Encrypt Transmission of Cardholder
data across open public networks (in
Flight SSL)
V.
Protect all systems against malware
and regularly update anti-virus
software or programs
VI.
Develop and maintain secure systems and applications
VII.
Restrict access to Cardholder data by
business need to know
VIII.
identify
and authenticate access to system components
IX.
Restrict Physical access to card holder data
X.
Track
and Monitor all access to network resources and card holder data
XI.
Regularly
test security systems and processes
XII.
Maintain a
Policy that addresses Information Security for all personnel
fdrfasbiptrm
ISO/IEC
27001 STANDARD
This
standard includes seven main titles within the scope of annex SL:
organization,
leadership,
planning,
support,
operation,
performance
evaluation and
improvement
olpsopei