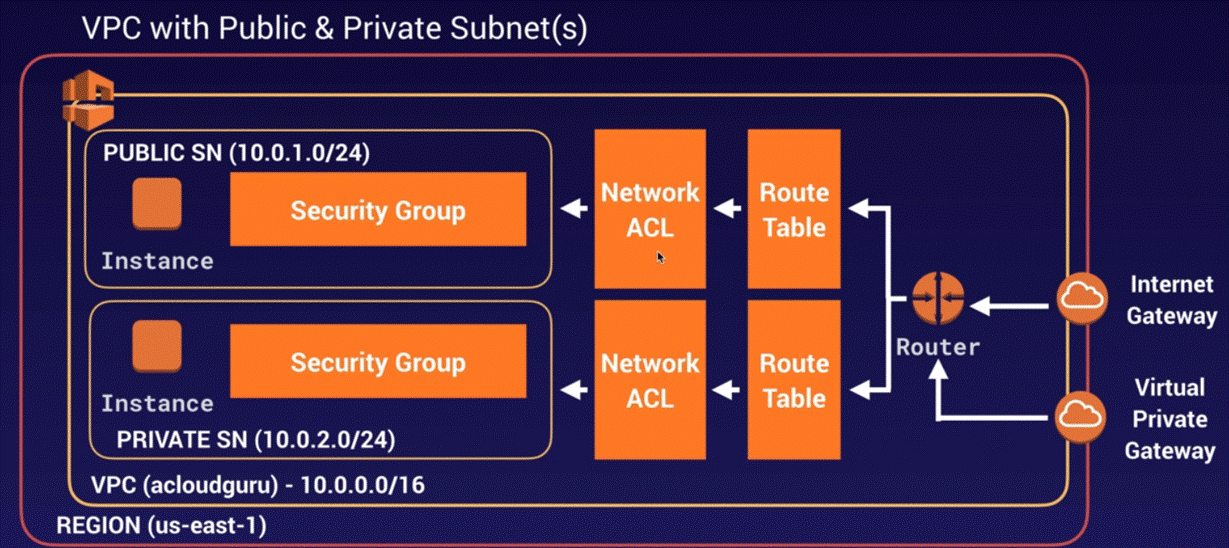
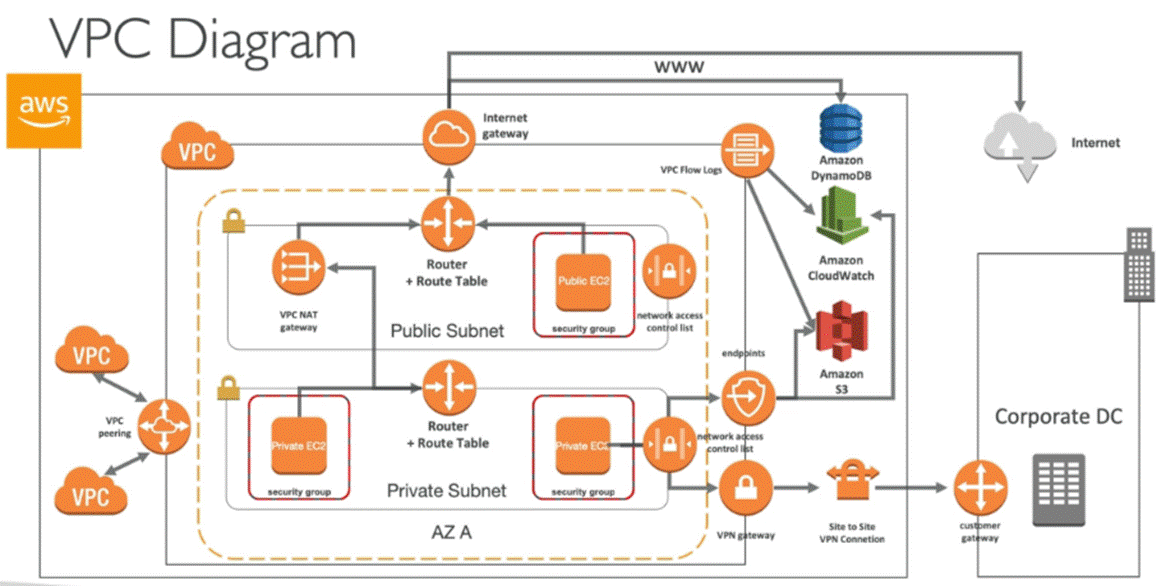
VPC
- A Virtual Private Cloud: A logically isolated virtual
network in the AWS cloud. You define a VPC’s IP address space from ranges
you select.
- Subnet: A segment of a VPC’s IP address range where you
can place groups of isolated resources.
- Internet Gateway: The Amazon VPC side of a connection to the public
Internet.
- NAT Gateway: A highly available, managed Network Address
Translation (NAT) service for your resources in a private subnet to access
the Internet.
- Virtual private gateway: The Amazon VPC side of a
VPN connection.
- Peering Connection: A peering connection enables you to route
traffic via private IP addresses between two peered VPCs.
- VPC Endpoints: Enables private connectivity to services hosted
in AWS, from within your VPC without using an Internet Gateway, VPN,
Network Address Translation (NAT) devices, or firewall proxies.
- Egress-only Internet Gateway: A stateful
gateway to provide egress only access for IPv6 traffic from the VPC to the
Internet.
VPC Classless
Internet Domain Routing (CIDR)
·
You assign a single CIDR IP address
range as the primary CIDR block when you create a VPC and can add up to four
(4) secondary CIDR blocks after creation of the VPC.
o Default VPCs are assigned a CIDR
range of 172.31.0.0/16, Default subnets use /20 CIDRs within the default VPC
CIDR
o initially limited to launching 20
Amazon EC2 instances at any one time and a maximum VPC size of /16 (65,536 IPs)
Subnet
o minimum size of a subnet is a /28
o You may create a default route for
each subnet
o
Internet
Gateway
o Horizontally
scaled, redundant and highly available VPC component that allows communications
within the VPC to the Internet
o
NACL -
Network Access Control Lists
o default
NACAL in VPC has allow inbound and outbound (stateless) ; only 1 NACL per
subnet
o Can
create custom ACL, by default disallows all inbound and outbound until rules
are added
o Each
subnet must be associated with a NACL
o Block
IP Addresses using NACL not Security Groups
Security
Groups
o Default
SG Deny all; one or many SG`s attached to one or many EC2s and SG are State full
o Take
effect immediately
o
NAT Instance:
(ec2 instance) when upgrading to a NAT gateway, make it in Public Subnet
NAT Gateway:
(redundant inside the AZ) can assign EIP, but must select the subnet it goes in
o Ephemeral ports used for NAT Gateway 1024 -
65535
Peering Connections
o non
overlapping CIDR
o Peering connections can be created
with VPCs in different regions (excluding China)
o “Edge to Edge routing” isn’t supported in Amazon VPC.
o VPC peering connections do not require an Internet Gateway.
o cannot use another peered connections
NAT Gateway
o Can peer entire CIDR block or partial
·
Inter-Region
Peering connections
o Inter-Region
VPC Peering traffic is encrypted using AEAD (Authenticated Encryption with
Associated Data) algorithm
o Route 53 private DNS can be used to
resolve to a private IP address with Inter-Region
VPC Peering
o Security groups cannot be referenced
across an Inter-Region VPC Peering connection
o Inter-Region VPC Peering does not
support IPv6
o Network Load Balancers, AWS PrivateLink and Elastic File System cannot be used over
Inter-Region VPC Peering
VPC endpoints
·
A
VPC endpoint enables you to privately connect your VPC to supported AWS
services and VPC endpoint services powered by PrivateLink
without requiring an internet gateway, NAT device, VPN connection, or AWS
Direct Connect connection. Instances in your VPC do not require public IP
addresses to communicate with resources in the service. Traffic between your
VPC and the other service does not leave the Amazon network.
·
VPC Endpoint always has precedence
over Nat or Internet Gateway
·
An interface endpoint is an elastic
network interface with a private IP address that serves as an entry point for traffic
destined to a supported service. A gateway endpoint is a gateway that is a
target for a specified route in your route table, used for traffic destined to
a supported AWS service. It is important to note that for Amazon S3 and
DynamoDB service, you have to create a gateway endpoint and then use an
interface endpoint for other services
·
o Gateway Endpoints
§
A gateway endpoint is a gateway that
is a target for a specified route in your route table, used for traffic
destined to a supported AWS service. The following AWS services are supported:
§
Amazon
S3 - S3 Policy in the endpoint to associate which
bucket(s) can be accessed and also IAM
/user role from the resource allowed to access them
§
DynamoDB
-
o Interface Endpoints
(Powered by AWS PrivateLink)
§
An interface endpoint is an elastic
network interface with a private IP address that serves as an entry point for
traffic destined to a supported service.
egress-only
Internet gateway is for use with IPv6 traffic only.
Internet GW
Egress > like a NAt for IPv6
VPC Flow Logs is a feature that enables you to
capture information about the IP traffic going to and from network interfaces
in your VPC. Flow log data can be published to Amazon CloudWatch Logs and S3
o can
create at VPC, Subnet or Network Interface level; choice of accepted , rejected
or All log data
o Does
not monitor, DHCP, AWS DNS server instance interaction; Windows activation
traffic; 169.254.169.254 instance metadata; traffic to the reserved IP address
for the default router
o cannot
create VPC flow logs with a peered VPC unless it is in your account.
AWS PrivateLink is a networking feature provided by Amazon Web
Services (AWS) that eases and secures connectivity between Amazon Virtual
Private Clouds (VPCs), other Amazon cloud services and
on-premises applications
ClassicLink allows you to link an EC2-Classic
instance to a VPC in your account, within the same region. This allows you to
associate the VPC security groups with the EC2-Classic instance, enabling
communication between your EC2-Classic instance and instances in your VPC using
private IPv4 addresses. ClassicLink removes the need
to make use of public IPv4 addresses or Elastic IP addresses to enable
communication between instances in these platforms